Back to Vendor Directory
Onapsis
Onapsis is the global leader in SAP cybersecurity and compliance, trusted by the world’s leading organizations to securely accelerate their SAP cloud digital transformations with confidence. As the SAP-endorsed and most widely used solution to protect SAP, the Onapsis Platform empowers Cybersecurity and SAP teams with automated compliance, vulnerability management, threat detection, and secure development for their RISE with SAP, S/4HANA Cloud and hybrid SAP applications.
![]()
Featured Solutions
In this informative presentation featuring Roland Costea, CISO at SAP Enterprise Cloud Services (ECS), and Mariano Nunez, CEO & Co-Founder of Onapsis, you will discover how the people, processes, and technologies at SAP ECS combined with the Onapsis capabilities, empower customers to better secure their Cloud ERP systems and promote long term business resilience.
Latest security solution providing unmatched, comprehensive SAP code testing capabilities
Discover key insights, gain actionable advice, and empower your organization to navigate the cloud securely during this conversation with industry experts from Onapsis and Capgemini.
Featured Content
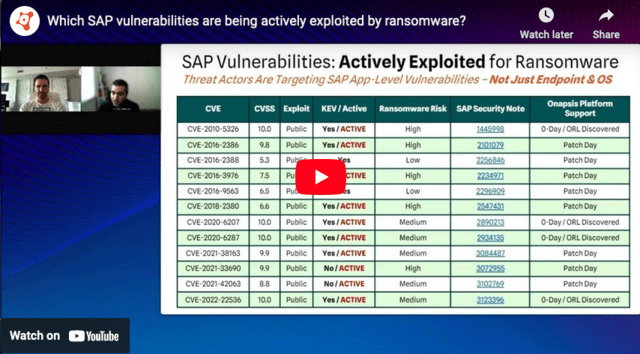
Join cybersecurity leaders from EclecticIQ, Mandiant, NightDragon, and Onapsis as they dissect the recent wave of SAP zero-day attacks and provide proactive defense strategies
We partnered with SAP Press to deliver the definitive guide to Cybersecurity for SAP
Multimedia Center
Onapsis and Flashpoint released a report detailing how cybercriminals are increasingly discussing and targeting SAP applications.
In this webinar, learn how enhanced visibility, automated security scanning, and incident response can augment your team’s ability to inspect what they expect from RISE with SAP, increase business value, and promote risk abatement.
Articles / Case Studies / Videos
Why Security Timing Determines Success in RISE with SAP TransformationsSecurity timing often determines whether RISE with SAP transformations stay on track. This analysis examines how late risk discovery undermines migration, execution, and post–go-live outcomes, and why secure-by-design approaches change delivery discipline.
Automating DevSecOps to Better Secure SAP SystemsThe rise of cyber threats targeting ERP systems necessitates an urgent shift towards integrated security within SAP development processes, as Onapsis updates its platform to enhance code security, transport governance, and runtime protection for enterprise resilience.
SAPinsider Benchmark Research – RISE with SAP 2025As 2025 ends, the narrative around SAP migration has shifted from “why move?” to “how fast?”
This SAPinsider report, based on a survey of 122 community members conducted in late 2025, highlights a marked acceleration in cloud ERP adoption as the 2027 end-of-maintenance deadline approaches.
Now commercially referred to as SAP Cloud ERP Private, the RISE with SAP package is seeing varied adoption rates; smaller organizations (under $2 billion in revenue) are currently twice as likely to be live on the solution compared to larger enterprises, which are predominantly in the planning or exploration phases.
While SAP’s dedicated transition support and license conversion credits are the primary drivers for migration, cost and unclear business value remain significant barriers for holdouts. The report also identifies a growing influence of Generative AI on ERP strategy. However, it warns of critical gaps in security compliance and an impending shortage of skilled implementation resources.
Download the benchmark report to read the full data analysis and receive recommendations for your own plans.
- Understand why there is a concerning lack of security awareness
- Why we forecast that implementation partners will struggle to staff the volume of concurrent projects required to meet the 2027 and 2030 deadlines.
- How SAP’s direct support and financial incentives are driving adoption rates
Reviewing Zero-Day Vulnerabilities in SAPIn March 2025, cybersecurity firms detected exploitation activities linked to a critical zero-day vulnerability in SAP NetWeaver, leading to a swift patch by SAP, but many organizations had already suffered significant impacts, emphasizing the urgent need for improved visibility, auditing, and responsiveness in securing SAP systems.
Onapsis and Microsoft Partner to Provide End-to-End SAP Security MonitoringOnapsis has launched an integration between Onapsis Defend and Microsoft's Sentinel SIEM platform to enhance threat detection and response for SAP applications, addressing security challenges by providing SOCs with unified visibility and enriched threat intelligence.
New Onapsis Platform Updates Deliver Deeper SAP SecurityAs SAP systems face increasing cyber threats, Onapsis has announced new functionality in its platform to enhance security and patch management, emphasizing the importance of prioritizing SAP protection, securing executive support for cybersecurity initiatives, and adopting a layered defense strategy.
SAPinsider Benchmark Research Webinar – RISE with SAP 2025A Market Divided and a Looming Resource Crunch
Organizations are facing a pivotal moment as the shift to SAP Cloud ERP accelerates and the end of maintenance for core SAP ERP systems nears. SAPinsider’s latest RISE with SAP Benchmark Research reveals how companies are responding to rising pressure to modernize, the reasons behind their adoption decisions, and the challenges they must overcome. With two thirds of respondents already running, deploying, or exploring SAP Cloud ERP, the findings offer an in-depth look at what is driving ERP transformation in 2025 and where organizations are investing to prepare for the future.
In this session, SAPinsider analysts walk through the key data shaping cloud ERP strategy, including the role played by SAP Cloud ERP Private (RISE with SAP), the impact of AI capabilities such as Joule, and the realities of skills shortages, security requirements, and cost considerations. Attendees will gain a research-driven view of how peers are planning, executing, and governing their transitions, along with practical insights they can use to guide their own ERP roadmaps.
Watch this session to:
- Understand what is driving organizations to accelerate their move to SAP Cloud ERP Private and how adoption differs by company size.
- Learn why support from SAP, access to new functionality, and the rise of generative AI are shaping decision making.
- Hear which challenges organizations say are most difficult, including data cleansing, custom code remediation, and securing business support.
- See how companies are forming strategy teams, involving executives, and preparing for resource shortages in the coming years.
- Gain guidance on the steps organizations should take now to prepare for ERP transformation and long term innovation.
Critical SAP Zero-Day Vulnerability Under Active ExploitationActive exploitation of a critical zero-day vulnerability (CVE-2025-31324) in the SAP Visual Composer component allows unauthenticated attackers to gain full control over SAP systems, prompting SAP to release an emergency patch and urging customers to either apply it or disable access to the vulnerable component.
Understanding Threat Actors Attacking SAP with OnapsisIn April 2024, Onapsis, in collaboration with Flashpoint, released the 'Ch4tter: Threat Actors Attacking SAP for Profit' report, emphasizing the evolving cybersecurity risks facing SAP organizations and advocating for proactive measures like penetration testing and ongoing education to mitigate these threats.
Beyond Patching: Building a Multi-Layered Defense for Your SAP LandscapeThis whitepaper provides SAP users and CISOs with best practices for securing SAP systems, emphasizing the importance of a multi-layered defense strategy that goes beyond traditional patching. It offers insights into the multifaceted aspects of SAP cybersecurity to help organizations protect their critical SAP landscapes.
Ensuring Security is at the Heart of a Clean Core StrategyAs companies transition to SAP S/4HANA under the Clean Core strategy to streamline operations and reduce legacy complexity, they must also navigate new security challenges associated with increased customization and cloud integrations, prompting collaboration with security partners like Onapsis to maintain a secure and efficient environment.
Onapsis Announces New Cybersecurity Book to Debut at SAPinsider Vegas 2025At SAPinsider Vegas, technology leaders will gather to explore SAP landscape optimization and cybersecurity, highlighted by the release of Onapsis's new book 'Cybersecurity for SAP,' co-authored by its CTO and focused on addressing security challenges amid rising cyber threats.
From Discovery to Defense – Securing SAP with OnapsisMariano Nunez transformed his passion for cybersecurity into leadership at Onapsis, a company he founded to enhance SAP security against evolving cyber threats, emphasizing the necessity of proactive measures and collaborative frameworks as organizations migrate to the cloud.
Onapsis Announces New Secure RISE AcceleratorOnapsis has launched the Secure RISE Accelerator to enhance cybersecurity and compliance during RISE with SAP transformations by automating processes, conducting risk assessments, and providing expert support, thus enabling organizations to innovate securely and efficiently.
Bolstering Cybersecurity and Resilience with OnapsisAs the average cost of an SAP data breach rises to $10 million, organizations must enhance their cybersecurity strategies by focusing on technology, processes, and skilled personnel, while leveraging RISE with SAP along with Onapsis to effectively manage cloud security risks.
Onapsis Announces Security Testing Solution: Control CentralOnapsis has launched Control Central, a new product within its Control suite that enhances application security testing for RISE with SAP transformations by automating code scanning, reducing manual tasks, and aiding organizations in securing their SAP environments against vulnerabilities.
Onapsis Announces Enhanced Security Features for SAP BTPThe SAP cybersecurity specialists at Onapsis announced that they have expanded their Control product line to feature a bundle that bolsters the security of SAP Business Technology Platform (BTP). This new solution allows users to automatically scan code for potential threats throughout a number of environments and depositories. The product is available as of Q4 […]
Fortune 500 Utility Company Partners with Onapsis to Build Security into Their RISE with SAP Transformation and Achieve Secure, On-Time, On-Budget Go-LiveA Fortune 500 utility company, facing challenges with their legacy SAP system, chose the RISE with SAP program for a clean migration to SAP S/4HANA, recognizing the need for enhanced security skills and expertise, and found a trusted partner in Onapsis to provide the necessary support and technology for their transition.
Securing SAP Remote Function Calls: The Crucial Role of S_ICF AuthorizationThe article discusses the importance of the S_ICF authorization object in SAP systems as a security measure to mitigate RFC hopping attacks by controlling access to RFC destinations and ensuring that only authorized users can initiate function calls, thereby reducing the risk of unauthorized privilege escalation following a cyber attack.
Hash Cracking and the SAP LandscapeThis article discusses the use of hashing for password security in SAP systems, explaining how hashes are stored, methods for cracking them using tools like JohnTheRipper and Hashcat, and emphasizes the importance of addressing weak hashes and deactivating downward compatibility to enhance data protection.
83% of Organizations experienced at least one ransomware attack in the last yearA recent report reveals that 83% of organizations faced ransomware attacks in the past year, with significant impacts on ERP systems, prompting 93% to seek dedicated ERP security solutions, while concerns grow over AI-enhanced threats and organizations increasingly adjusting their cybersecurity strategies and investments.
ERP Security for Utility Companies – Onapsis Partners with SNOPUD to Secure Critical SAP ApplicationsCyberattacks on utility companies are increasingly targeting vulnerabilities in SAP applications, posing significant financial and operational risks, with the average cost of a data breach reaching $4.72 million. The energy sector, with its sensitive enterprise resource planning (ERP) systems like SAP, is particularly attractive to cybercriminals. Despite this, many utility companies struggle to allocate adequate resources for security, especially amid ongoing digital transformation efforts. The consequences of such attacks can be severe, leading to business disruptions, power or water outages, and the theft of customer data. To address these challenges, Onapsis, a leader in business application security, has partnered with Snohomish County Public Utility District (SNOPUD) to enhance SAP security through its Connect Up initiative, aimed at upgrading meters across homes and businesses. This collaboration leverages Onapsis' threat intelligence and automated vulnerability remediation to safeguard SNOPUD's critical systems and customer data, supporting a security-first approach as the utility modernizes its operations.
Augmenting Existing SAP Network Security with OnapsisA recent study by Onapsis highlights a 400% rise in ransomware incidents targeting SAP systems, emphasizing the critical need for enhanced security measures to protect these applications. SAP offers various security features, including user authentication, encryption, and monitoring controls like SAProuter. However, if compromised, SAProuter can be an entry point for unauthorized access. Traditional vulnerability management and security monitoring often fall short for SAP systems, leading to a lack of visibility and effective threat detection. Onapsis addresses this gap with its automation capabilities and in-depth threat intelligence from Onapsis Research Labs. Key Solutions offered by Onapsis include Onapsis Assess that supports SAProuter, extending vulnerability management with automated scans and risk-driven analysis. This enables better prioritization and faster response to potential threats without manual intervention. Similarly, Onapsis Defend continuously monitors SAProuter for insider threats and potential compromises. It swiftly detects unauthorized access through targeted alerts and monitors over 2,000 threat indicators, including zero-day threats.
The Onapsis Platform operates independently of SAP systems, ensuring security without compromising performance. It offers visibility into critical SAP systems, helping teams manage security, compliance, and availability issues through advanced analytics, reporting, and automation tools.
Vulnerabilities Affecting SAP AI ServicesOn July 17th, 2024, Hillai Ben-Sasson, a security researcher from the cloud company WIZ released the results of a research focused on SAP Cloud AI services, which was part of a broader research around mainstream AI cloud providers also including Hugging Face and Replicate. The researcher identified a set of weaknesses in the cloud infrastructure of the SAP Core AI service.
Lessons from Onapsis-Flashpoint Report and BeyondIn the realm of enterprise resource planning (ERP) systems, security is a constant battleground. Despite the availability of patches for known vulnerabilities, the Onapsis-Flashpoint Ch4tter report sheds light on a worrying trend: increased attack activities on these critical systems.
Protecting SAP Solutions from Cyber Threats with OnapsisRecent SAPinsider research highlights that protecting sensitive data in SAP systems is a major concern for SAP customers. Traditional security efforts focused on managing access, but new research by Onapsis and Flashpoint reveals an increase in cyber threats targeting SAP systems. Ransomware incidents have surged by 400%, and discussions about SAP vulnerabilities on various web platforms have increased by 490% from 2021 to 2023. Patching remains a challenge due to the need to balance system availability with downtime. Onapsis emphasizes the importance of integrating SAP into existing security programs, conducting regular vulnerability assessments, applying security patches promptly, and maintaining continuous security monitoring. Additionally, a secure development lifecycle and robust threat intelligence are essential for protecting SAP applications from evolving threats.
Related

- RISE with SAP
- SAP ABAP
- SAP ABAP Test Cockpit
- SAP Application Development and Integration
- SAP Basis
- SAP CIO
- SAP Code Inspector
- SAP CyberSecurity
- SAP Data Security
- SAP Development Tools
- SAP DevOps
- SAP Digital Transformation
- SAP Disaster Recovery
- SAP ECC 6.0
- SAP ECC Migration
- SAP Enterprise Threat Detection
- SAP ERP
- SAP Fiori
- SAP Governance Risk and Compliance
- SAP GRC
- SAP Identity Management
- SAP Process Control
- SAP QA
- SAP Quality and Testing
- SAP Regulatory Compliance
- SAP S/4HANA
- SAP Security
- SAP SOX Compliance
- SAP UI5
- SAP Vulnerability Analysis
- Show More
Your request has been successfully sent